Designing a Cloud Infrastructure.
should have's while designing/implementing cloud infrastructure.
Hey guys!
Thanks for joining. So we would go on an overview of what designing an infrastructure entail.
As per prerequisites, Basic knowledge of cloud computing would do.
Introduction
Designing a cloud infrastructure for your workload gives in-depth schematics to the engineers and stakeholders involved in the project. The Design shows the resources that would be created or might have been in existence and how all resources work to meet Company's objectives.
For instance, If the Company is designing its cloud Infrastructure to achieve high availability or for cost optimization.
Kindly note that the basics of this course content apply to all cloud platforms.
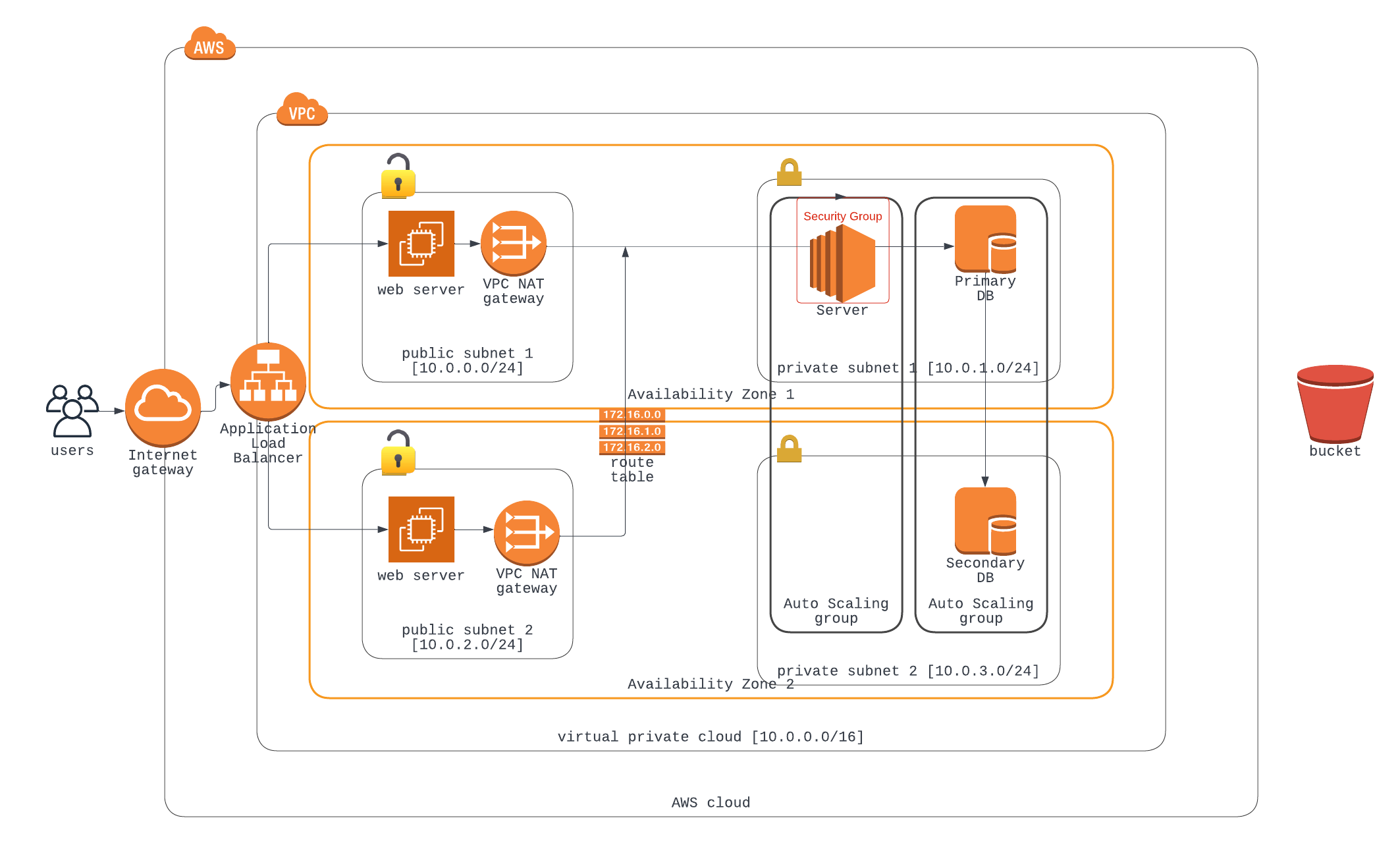
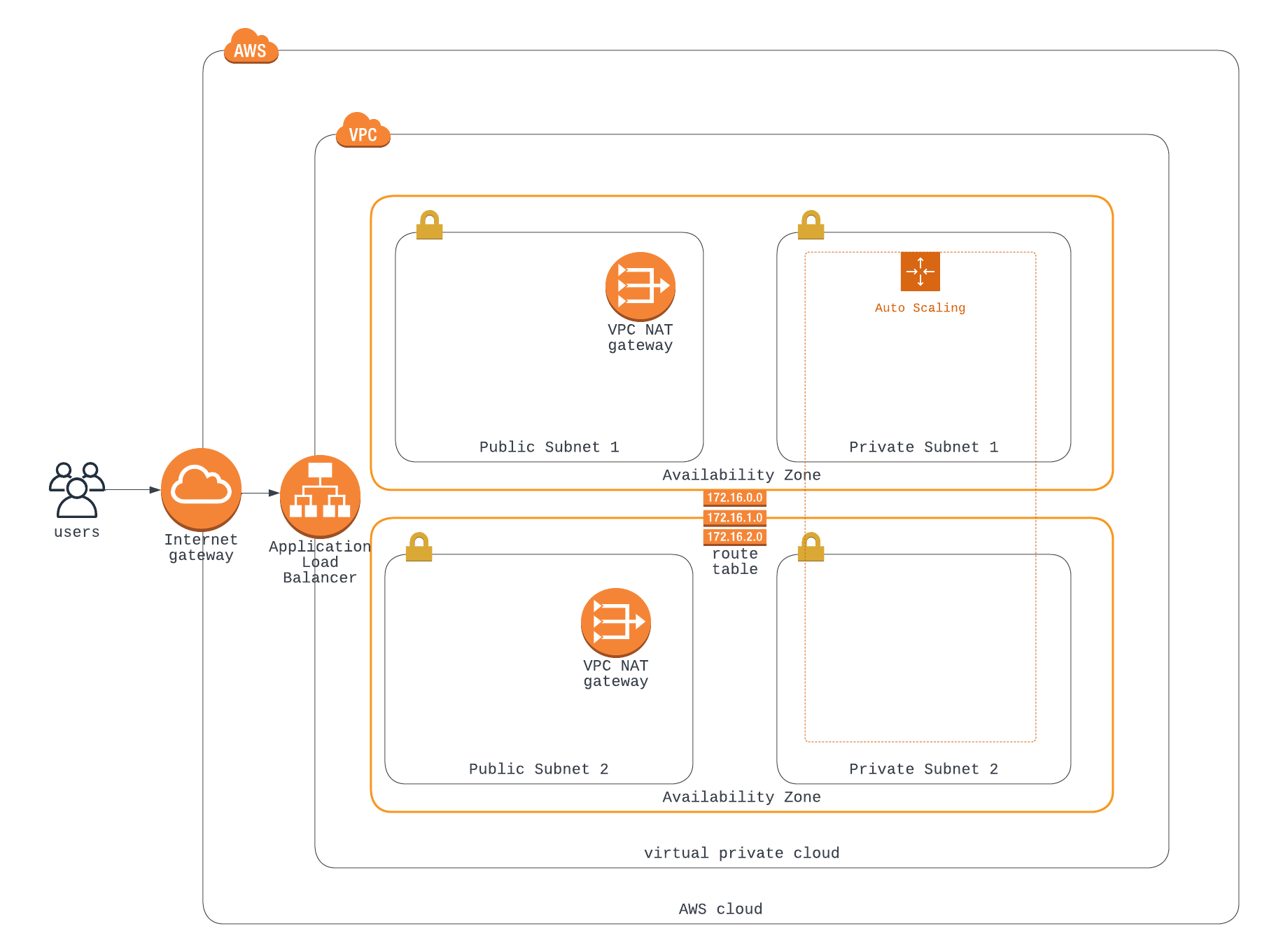
Below is a complete display of the Infrastructure we plan to design and implement.
 So let's go through some of the most haves while designing an infrastructure.
So let's go through some of the most haves while designing an infrastructure.
Region
A region is a physical location, more like a data center, which would house your compute resources. It is nice to instantiate more than one for resiliency's sake.
So after the successful setup of your cloud account, we have to specify which region or multi-region would house your infrastructure.
Regions are mainly chosen based on the location closest to the intended users to aid low latency and high availability of resources.
Kindly note this is not represented by an outline in the design.
VPC
Virtual Private Cloud can be referred to as an isolated networking container that wraps around our entire resource. (as indicated in the diagram within our cloud).
Although in a more elaborate sense, it's a block of available IP addresses known as address space, the CIDR block refers to the number of IP addresses available for you to deploy resources within your private network. Resources such as Linux servers, windows servers, databases, etc., and each server/resource would require an IP address space within the VPC.
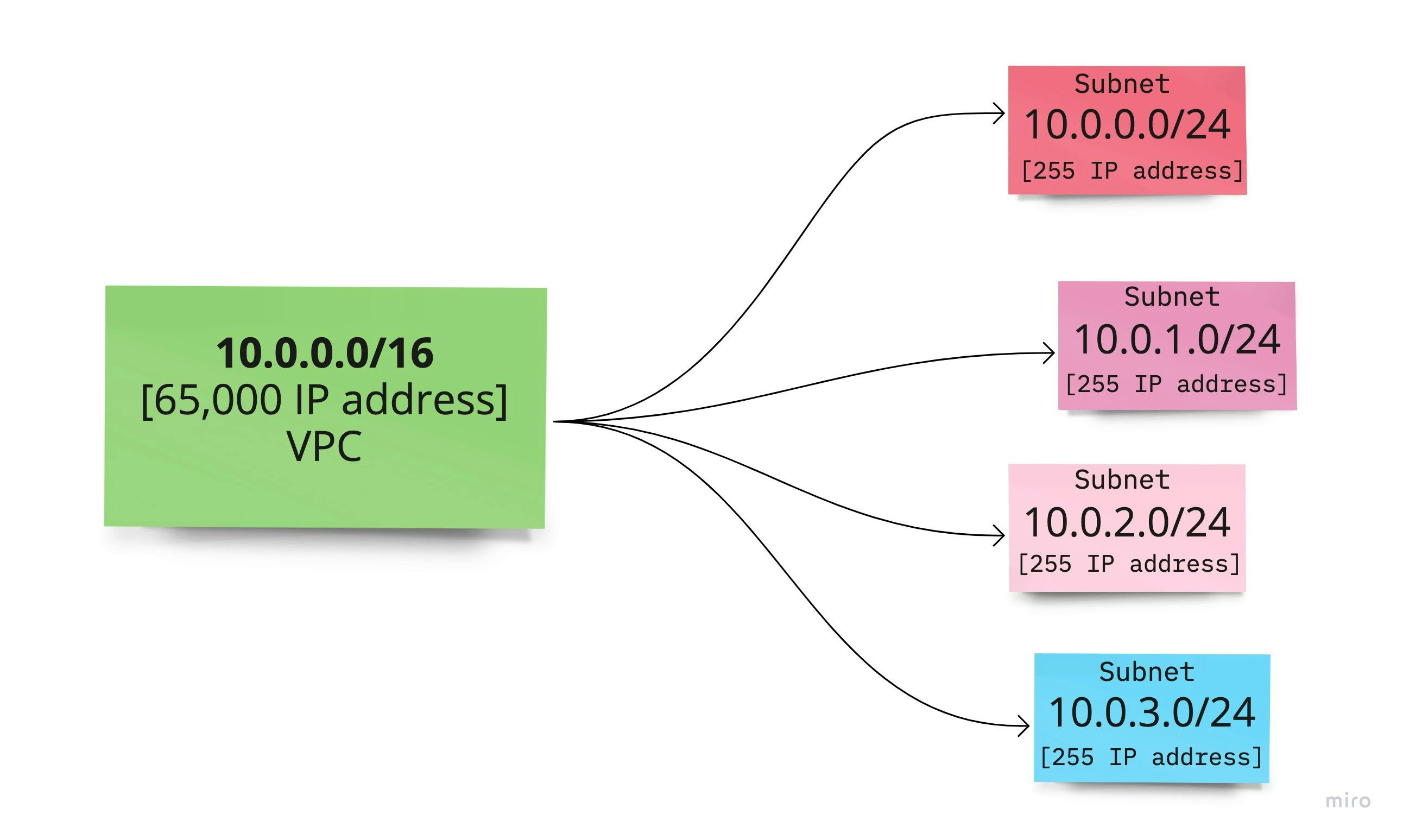
for example, creating a VPC with the CIDR block.
10.0.0.0/16
This would give us a sum total of about 65,535 available IP address spaces.
SUBNET
A Subnet is a subset of the available IP addresses which helps create logical separation between resources, for instance, it can help us separate the production stage from the development stage.
It helps restrict/allow access from/to a group of resources through routing and can provide service to a specific set of resources.
RECAP of VPC & SUBNET
- VPC provides you with a private IP address for your networking resources.
- A subnet is a small network space of your available IP address space.
/00represents the number of constant bits from VPC or Subnet.- Subnet helps with routing to a specific group of resources
- While creating VPC and subnets keep in mind future expansion.
Note, VPC can cover several Availability Zones.
In the diagram, we have our VPC wrapping around two availability zones, and inside the availability zones, we have respective subnets specific to serve the zone.
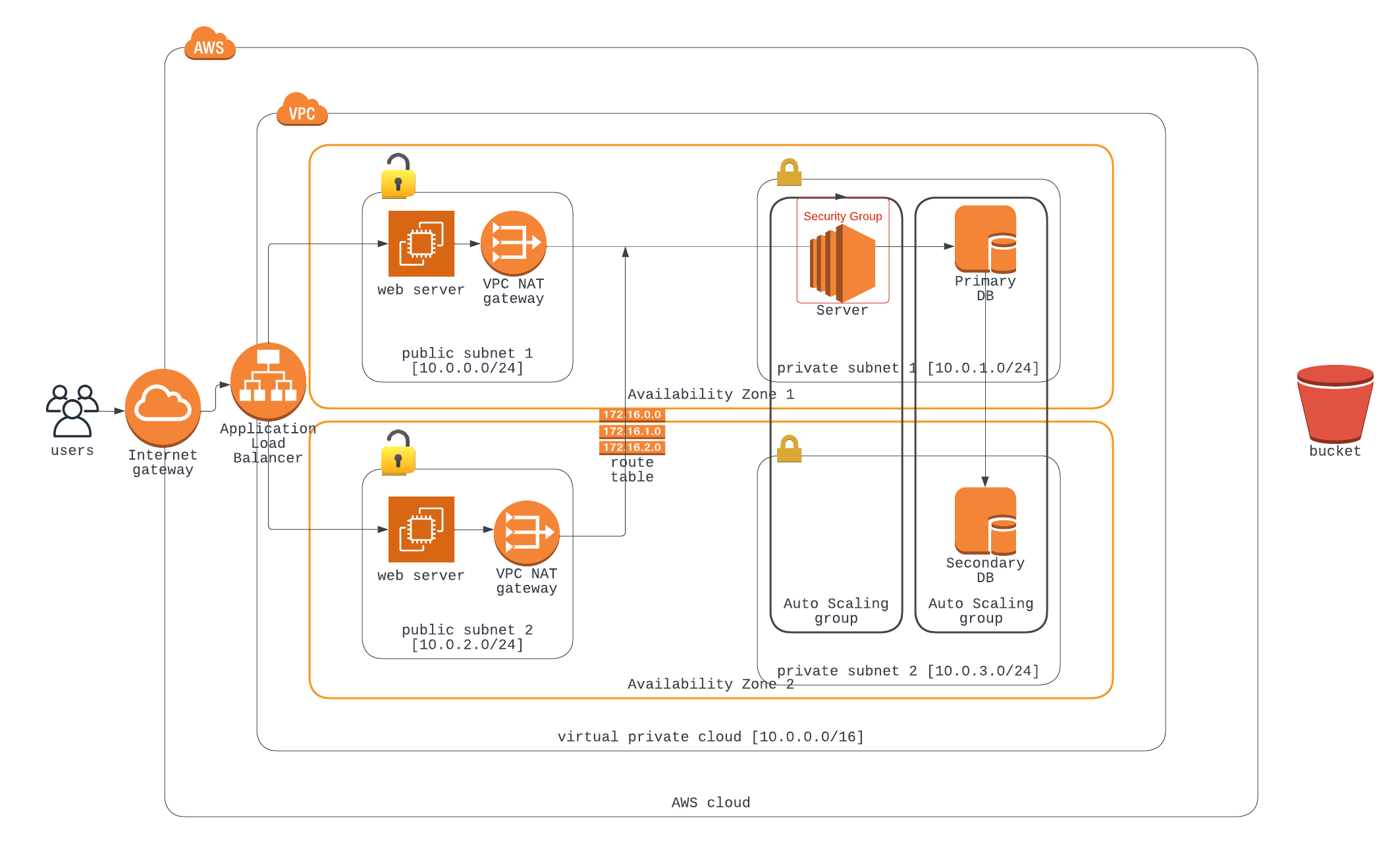
From the diagram, we have a public and private subnet in an availability zone. The main aim of creating multiple subnets is to use their IP address for routing traffic.
Let's take, for example, we deploy our front-end web app to the public subnet that is accessible to anyone on the internet and keep our database server that consists of sensitive data in a private subnet. By doing this, we can introduce routing rules and a security group to help restrict access to the subnet where our database is.
Internet Gateway
Since we know a VPC is an isolated network, so we need a pathway to the VPC since we have resources needed to be accessed. The internet gateway provides inbound and outbound traffic to the VPC.
Internet gateway enables inbound and outbound traffic from the internet to your VPC, and it allows external users to communicate with a part of your VPC.
If we want to provide internet access in our private network since the servers might need to download software patches or configuration changes that come from the public internet, a gateway is necessary.
Although answering the question if the cloud is needed when you have private resources you don't plan on sharing with the public? The answer is Yes. Although you wouldn't need an Internet gateway instead a VPN connection or direct connect connection would be quite useful.
Software-defined networking is the act of using APIs and already existing physical infrastructure to create our networking layer with privacy rules, our routing, and private address space.
Direct Connect: is a physical data line that you can purchase directly from AWS through a telecom service provider in other to access your cloud platform (AWS, GCP, Azure, etc.) without moving your data traffic through the internet.
NAT Service
Which is added in both Availability Zone public subnet help improve High Availability and eliminates single point of failure.
The NAT gateway serves as an intermediary to take a private resource's outbound request, connect to the Internet gateway, and then relay the response back to the private resource without exposing that private resource's IP address to the public.
A Network Address Translation service provides outbound internet access to resources in the private subnet.
It translates Incoming public traffic into private traffic. You might be asking why it is kept in the public subnet if it's meant to provide outbound service to the private subnet?
It's simple, the sole reason for putting it in the public subset is that the NAT service itself, requires public access for it to function that it can't get from being isolated within the private network. So you have to place it in the public subnet. Kindly note.
Let's take, for instance, a resource in our private subnet (i.e. our Backend Service) that needs some data from the internet (example google.com).
It would place a request to the NAT gateway which would translate the private network request into a public request that goes through the internet gateway, and the response data would come back to the NAT service which would translate it back to a private response that our server can see in the private subnet.
Note Private Subnets consists of only private IP assigned resource which means they can't be exposed to the internet by themselves and therefore require the NAT service in other to communicate with the internet.
But Note any server in the public subnet can communicate with servers in the private subnet as long as they are in the same network.
Adding Servers
Let us add a couple of EC2 in both availability zone public subnet which would be our web server and has to be accessible to the public internet. but since we have an identical instance in both availability zone, we have to provide a united front that gives the public a unified access point to our web server therefore we introduce a load balancer.
Load Balancer is a service designed to distribute the workload amongst a group of servers that provide a common service. I.e. If the autoscaling group spins up 10 new servers, the load balancer would distribute traffic/workload to those instances. Load Balancers also perform a health check and replace non-functional servers with a new instance. Without Load Balancers, it would be impossible to have a public-facing server in more than one Availability Zone.
Kidly note you can also associate a load balancer with an auto-scaling ground.
Auto Scaling Group: this is used to manage servers that provide a common service. Auto Scaling needs more than one subnet to carry out its function and it ensures high availability and elasticity. In case of failure of resource at the private subnet in AZ1, the auto-scaling group would spin up an identical server in the AZ2 private server. It is recommended that the autoscaling group should span more than one AZ for reliability.
 So let's go through some of the most haves while designing an infrastructure.
So let's go through some of the most haves while designing an infrastructure.
Security Group
A security Group is applied at the level of the instance or server is set to protect. for instance, in our diagram, the security group is set to provide network traffic control to the EC2 instance in our private subnet. Its default operation is to all ports and opens just port 80. It can be assigned to protect Load balancers, servers, and databases.
Although In case you plan on restricting traffic at the network/subnetwork level, you can make use of the Access Control List (ACL). But for restricting traffic/access to an instance, you have the security group for that.
Routing Table
This is a set of entry rules associated with one or more of your subnet inside your VPC. these rules allow us to deny traffic to/from the address range specified. The rules set can be open to the entire internet or restricted to a single IP address.
In our diagram, we make use of the routing table to make the private subnet accessible to the internet via specifying routing rules.
examples of rules.
All inbound/outbound traffic is allowed provided it with the VPC. In the instance where the private servers are sending a request to the internet, we would allow outbound traffic only for the private subnet and route internet traffic from the private subnet from any server going through the NAT. Which is much easier for public servers which can send both inbound/outbound through the internet gateway.
Note that our S3 bucket is kept outside our VPC because it is a publicly available service.
Check out the networking implementation with cloud formation [github.com/gbengafagbola/Infrastructure-as-...
Just for example's sake, how to add a resource (security group)
Type: AWS::EC2::SecurityGroup
Properties:
GroupDescription: String
GroupName: String
SecurityGroupEgress:
- Egress
SecurityGroupIngress:
- Ingress
Tags:
- Tag
VpcId: String
NB. In the security group setup, GroupDescription is the only compulsory entry. But this is out of the scope of this tutorial. thanks for following through and kindly stay tuned 😌.